Your web browser holds a treasure trove of personal information, from passwords and search history to financial details. Similar to how malicious apps can compromise your phone or computer, harmful browser extensions can expose this sensitive data. Recent reports reveal a concerning campaign targeting browser extensions, jeopardizing millions of users.

How Malicious Extensions Operate
Hackers employ various tactics to exploit browser extensions. Phishing campaigns targeting extension developers are common. By tricking developers into granting access, attackers inject harmful code into legitimate extensions. This code can then steal cookies, access tokens, and other valuable user data.
Cybersecurity firm Cyberhaven brought this campaign to light after one of their employees fell victim to a phishing attack. The attackers subsequently published a malicious version of the extension. Once these compromised extensions pass the platform's security review, they become available to a vast user base, significantly increasing the risk of data theft. These malicious extensions can monitor user activity, exfiltrate browsing data, and even bypass two-factor authentication.
Adding another layer of complexity, some developers might unknowingly incorporate data-gathering code within monetization software development kits. This makes it challenging to discern whether a compromise resulted from a hacking campaign or a deliberate action by the developer.

Identifying and Removing Malicious Extensions
Secure Annex, a browser extension security platform, is actively investigating this campaign. They've compiled a list of compromised extensions. It's crucial to immediately remove any of these extensions if you have them installed.
Secure Annex maintains a publicly accessible Google Sheet detailing the identified malicious extensions, including their status (updated or removed). They continuously update this list as new threats emerge.
Removing Extensions from Google Chrome
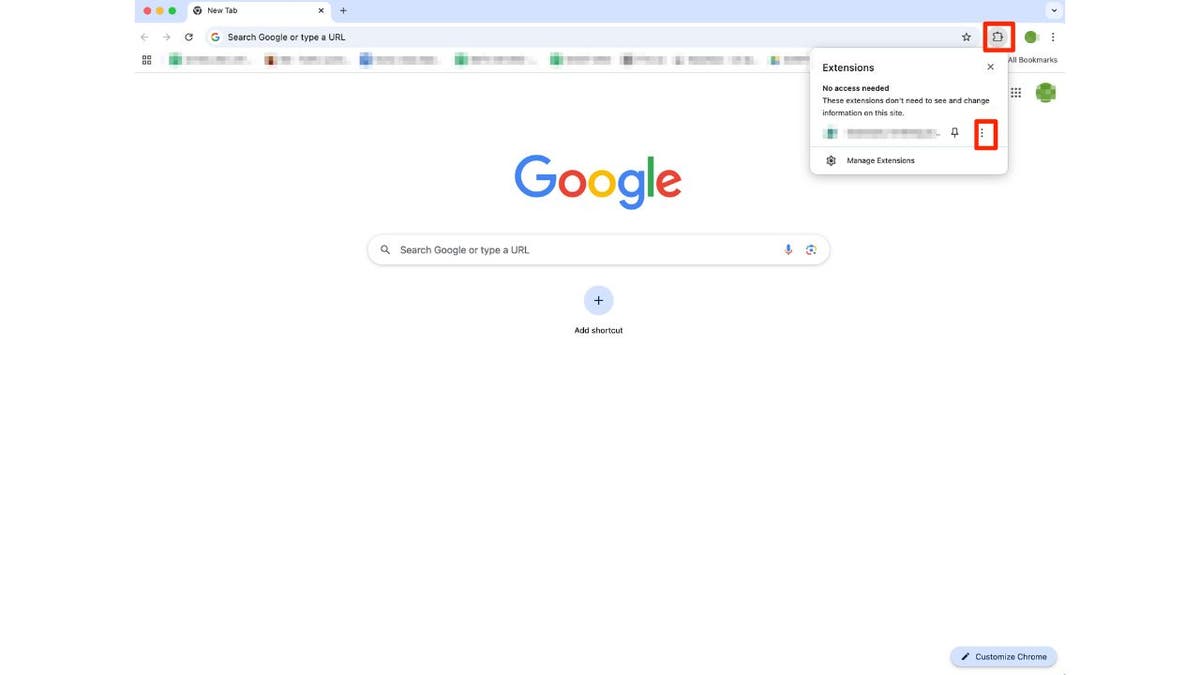
- Open Chrome and click the puzzle piece icon in the top-right corner.
- Locate the extension you wish to remove, click the three dots next to it, and select "Remove from Chrome."
- Confirm the removal by clicking "Remove."
Safeguarding Yourself from Malicious Software
- Scrutinize Emails and Links: Verify sender addresses and avoid clicking on suspicious links. Go directly to official websites when in doubt.
- Employ Robust Antivirus Software: Utilize reputable antivirus software to detect and block malicious code.
- Manage Extension Permissions: Carefully review and limit the permissions granted to extensions.
- Minimize Extension Usage: Only install essential extensions and regularly remove unused ones.
- Update Your Browser: Keep your browser updated to benefit from the latest security patches.
- Regularly Audit Extensions: Periodically review installed extensions and remove any that are no longer necessary or appear suspicious.
- Report Suspicious Activity: Report any suspicious extensions to the browser's extension marketplace.
Comments(0)
Top Comments